Last revision: December 07, 2019

NinjaScanner is a lightweight, fast and powerful antivirus scanner for WordPress which includes many features to help you scan your blog for malware and virus.
Features
- File integrity checker.
- File comparison viewer.
- Exclusion filters.
- File snapshot.
- Database snapshot.
- Anti-malware/Antivirus.
- Incremental scans.
- Background scans.
- Sandbox for quarantined files.
- Ignored files list.
- Scheduled scans.Premium
- WP-CLI integration.Premium
- Debugging log.
- Email report.
- Integration with NinjaFirewall (WP and WP+ Edition).
- Multi-site support.
- Contextual help.
- And many more…
As usual, we offer two open-source versions: a Free Edition and a Premium Edition with additional features and full support.
Summary page
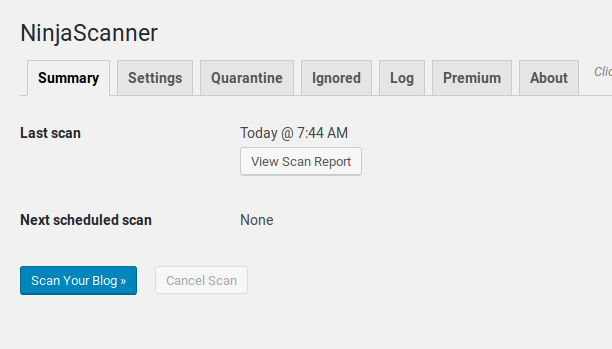
From the main summary page, you can start the scan, view the last report or the next scheduled scan date and time:
Basic Settings
You can quickly define here the most important options:
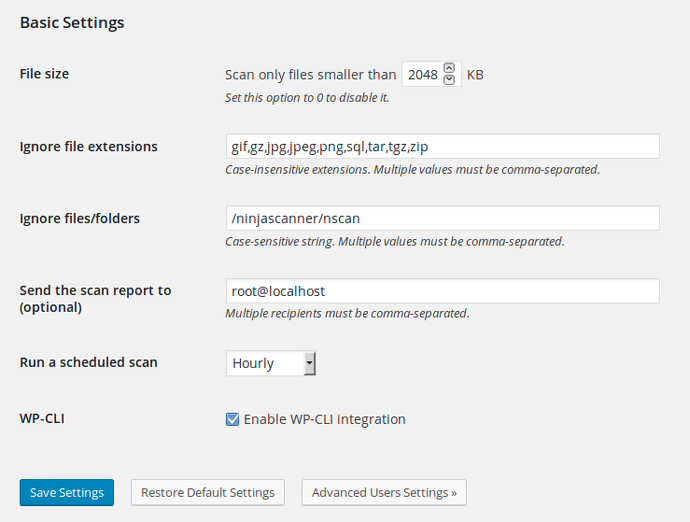
- File size / Ignore files Extensions / Ignore files & folders: These options do not apply to the File Integrity Checker (see “Advanced Settings” below).
- Send the scan report to: This optional feature will send a plain text copy of the scan report to one or more recipients by email.
- Run a scheduled scan and WP-CLI: See below.
Advanced Users Settings
These options let you finely tune NinjaScanner:
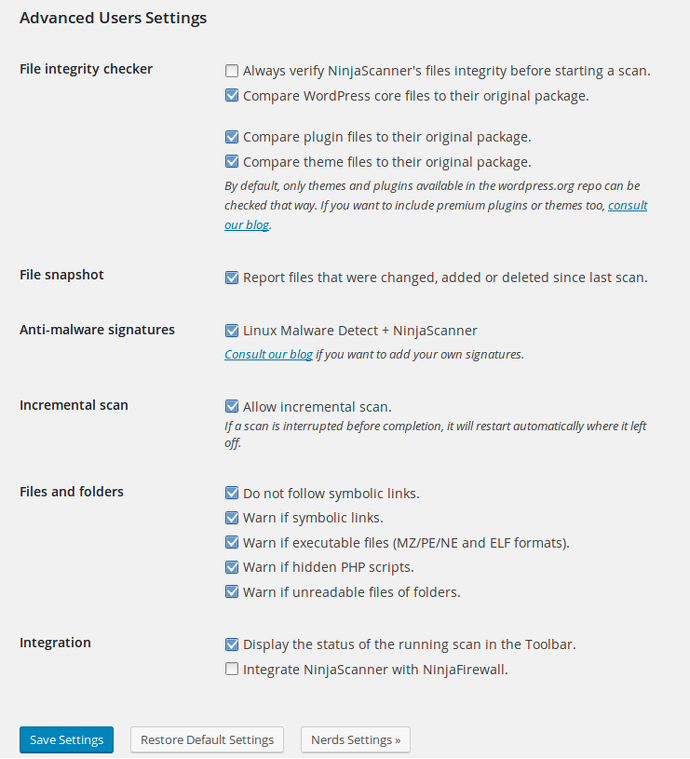
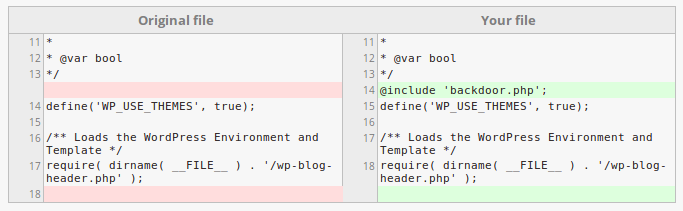
- File Integrity Checker: This option will compare the WordPress core files as well as your plugin and theme files to their original package. If one or more files do not match, they will be listed in the scan report:
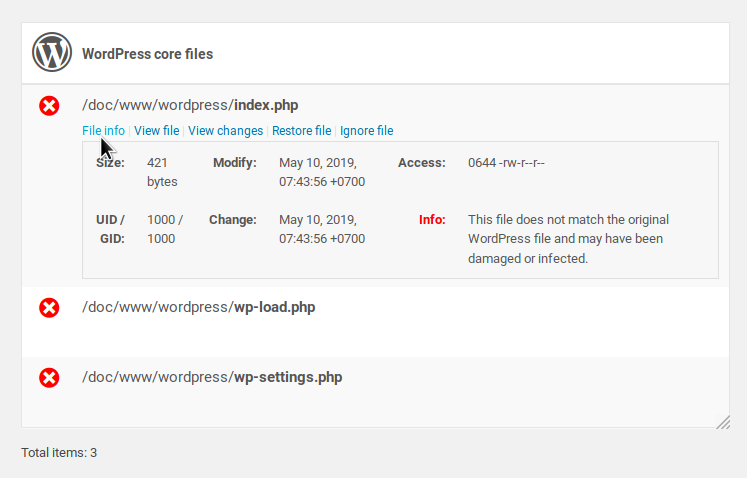
You can select a modified file and click on the “View changes” button to immediately compare it to the original one:
- File Snapshot: This option will show you which files were changed, added or deleted since the previous scan. It is pretty much similar to the “File Check” option from our NinjaFirewall plugin.
- Database snapshot: NinjaScanner will compare all posts and pages in the database with the previous scan and will report if any of them were changed, added or deleted.
- Anti-malware signatures: This option lets you scan your blog for potential malware and virus using the built-in signatures. The scanning engine is compatible with the popular Linux Malware Detect LMD (whose anti-malware signatures are included) and with some ClamAV signatures as well. You can even write your own anti-malware signatures (see below).
If you do not want to run the Anti-malware scan, simply disable all signatures checkboxes.
- Incremental Scan: If a scan is interrupted before completion (e.g., crash, error etc), it will restart automatically where it left off. This is a great feature hence we recommend to keep it enabled.
- Files and folders: Those options let you configure what NinjaScanner should do if it found symbolic links, hidden scripts, executable files etc.
- Integration: If you are running our NinjaFirewall (WP/WP+ Edtion)web application firewall, you can use this option to integrate NinjaScanner into its menu:
Nerds Settings
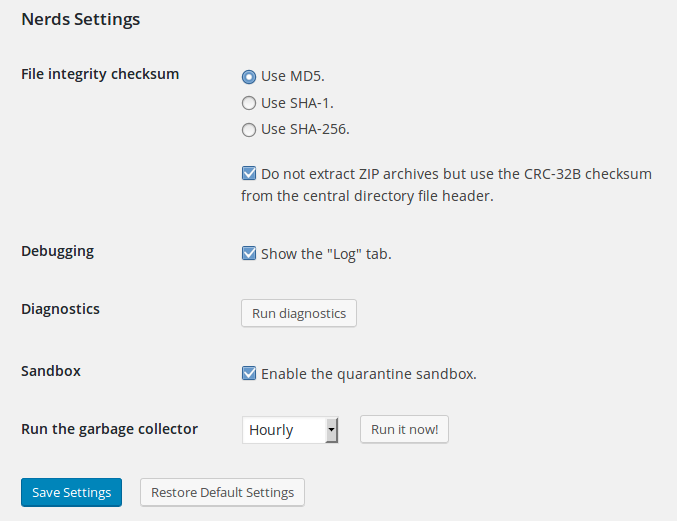
These settings are for hardcore users: make sure to understand what they do before enabling or disabling them (consult the contextual help for more info about each option).
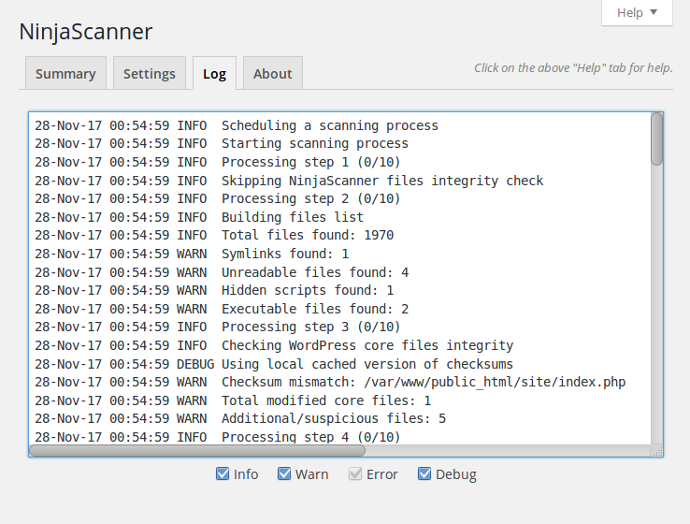
Enabling the scanner log can be helpful for debugging purposes:
Premium Features
Premium users can enjoy the following benefits:
- Scheduled Scans: Don’t leave your blog at risk. With the scheduled scan option, NinjaScanner will run automatically hourly, twice daily or daily.
- Dedicated Help Desk with Priority Support
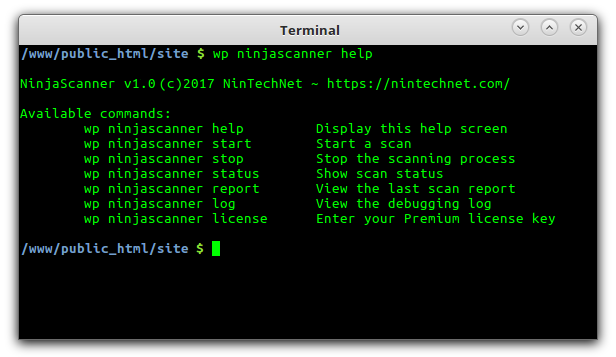
- WP-CLI Integration: Do you own several blogs and prefer to manage them from the command line? NinjaScanner can nicely integrate with WP-CLI, using the
ninjascannercommand. You can use it to start or stop a scanning process, view its status, its report or log and enter your Premium license key from your favourite terminal, without having to log in to the WordPress Admin Dashboard:
Get Premium now!
Fast and Lightweight Scanner
NinjaScanner has strictly no impact on your database. It only uses it to store its configuration (less than 1Kb). It saves the scan data, report, logs etc on disk only, makes use of caching to save bandwidth and server resources.
It also includes a Garbage Collector that will clean up its cache on a regular basis (it can be tweaked from the Nerds Settings page).
Background Scans
Another great NinjaScanner feature is that it runs in the background: start a scan, let it run and keep working on your blog as usual. You can even log out of the WordPress dashboard while a scanning process is running! You don’t have to wait patiently until the scan has finished.
Sandbox for quarantined files
When moving a file to the quarantine folder, NinjaScanner can use a testing environment (a.k.a. sandbox) to make sure that this action does not crash your blog with a fatal error. If it does, it will warn you and will not quarantine the file. It is possible (but not recommended) to disable the sandbox.
Adding Premium Themes and Plugins to the File Integrity Checker
Because the File Integrity Checker downloads themes and files from wordpress.org, it can, by default, only check open-source plugins and themes available from there. However, you can easily add your own plugins or themes (e.g., premium) to the File Integrity Checker.
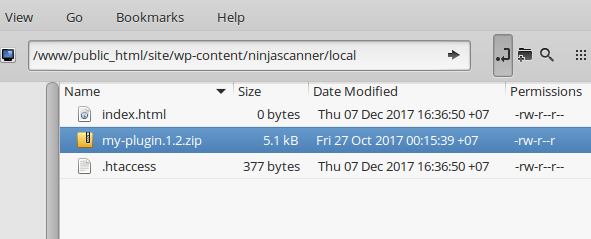
If your plugin slug is my-plugin and its version is 1.2, the file must be saved as my-plugin.1.2.zip. The same rule applies to themes.
- They must use the slug.version.zip format, as used by WordPress.org.
- The ZIP file must include the plugin/theme folder, a.k.a. slug (e.g.,my-plugin.1.2.zip/my-plugin/*)
- They must be uploaded into the
wp-content/ninjascanner/local/folder*.
* If you want to move the wp-content/ninjascanner/local folder to another location, eg., /foo/bar/local, you can do so by defining the NSCAN_LOCAL constant in your wp-config.php. The absolute path to that folder must be used:
define( 'NSCAN_LOCAL', '/foo/bar/local' );
When you update your premium plugin or theme, don’t forget to upload a new ZIP file!
NinjaScanner Troubleshooting
NinjaScanner should work out-of-the-box in most cases, but some hosting restrictions, e.g., server resource limits or security policies, may prevent it from working as expected. This article the most common issues a user may experience: NinjaScanner Troubleshooting
Adding your own anti-malware signatures
You can create and add your own signatures to the anti-malware. NinjaScanner’s engine supports two different formats:
1. HEX format
It is used by Linux Malware Detect and ClamAV antivirus. Signatures using that format start with the {HEX} keyword. Note that NinjaScanner does not support ClamAV wildcards (e.g., ??, a?, {n} etc). If you need to include wildcards, use the REX format below instead.
Signatures must follow this format:
{HEX}MalwareName:0:*:HexEncodedSignature
{HEX}: Signature keyword, must always be present.- MalwareName: This is your signature description that will be displayed by NinjaScanner if a positive detection occurs. You can use case insensitive alphabetic characters
a-zA-Z, digits0-9, as well as-,_and.characters. Do not use the colon character:because it is reserved. :0:*:: Extended signature format. Do not change this value.- HexEncodedSignature: This is the hexadecimal value of the signature you want to detect. Because it is hex-encoded, you can add either text based or binary signatures (i.e., to scan an executable program).
2. REX format
This is NinjaScanner’s own format, using hex-encoded regular expressions. Such signatures must start with the {REX} keyword and must follow this format:
{REX}MalwareName:0:*:HexEncodedRegexSignature
{REX}: Signature keyword, must always be present.- MalwareName: This is your signature description that will be displayed by NinjaScanner if a positive detection occurs. You can use case insensitive alphabetic characters
a-zA-Z, digits0-9, as well as-,_and.characters. Do not use the colon character:because it is reserved. :0:*:: Extended signature format. Do not change this value.- Hex-encoded regular expression (regex): This is the hexadecimal value of the regex signature you want to detect.
Loading the signatures
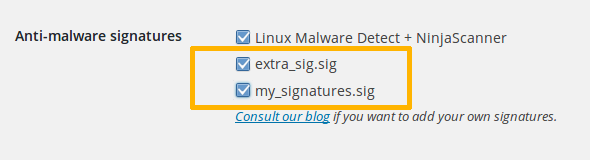
Your signatures must be written, one per line, and saved to one or more *.sig files which must be uploaded into the wp-content/ninjascanner/local/ folder.
You can see if your signatures are properly loaded from “NinjaScanner > Settings > Advanced Users Settings“:
Anti-Malware signatures generator
You can use the following form to create your own signatures:
Download
Download NinjaScanner: https://wordpress.org/plugins/ninjascanner/
