The WordPress WP Quick FrontEnd Editor plugin (1,000+ active installations) is prone to a broken access control vulnerability affecting version 5.5 and below that could lead to authenticated content injection, stored XSS and settings change among other issues.
This plugin does not seem to be maintained anymore and the vulnerability has never been fixed. Make sure to follow the recommendations below.
Authenticated Content Injection
In the “plugin.class.php” script L15, the plugin registers the AJAX save_content_front action with the WordPress wp_ajax_* hook:
add_action( 'wp_ajax_save_content_front', array($this, 'save_content_front') );
The save_content_front function, L269, calls the WordPress wp_update_post function but doesn’t check if the user is allowed to create or modify the corresponding post or page:
function save_content_front(){
extract($_REQUEST);
print_r($_REQUEST);
$thumb_id = get_post_thumbnail_id( $id );
if ( isset($imagesrc) && $imagesrc != '' ) {
set_post_thumbnail( $id, $imageid );
} else{
delete_post_thumbnail( $id );
};
$my_post = array(
'ID' => $id,
'post_title' => $title,
'post_content' => $content,
);
wp_update_post( $my_post );
die(0);
}
An authenticated user can edit/create any page or post on the blog.
Additionally, because the function lacks a security nonce, the call to the print_r() function L272 is prone to a reflected XSS via a CSRF attack.
Authenticated Settings Change and Stored XSS
In the same “plugin.class.php” script L17, the plugin registers the AJAX la_save_front_editor action with the wp_ajax_* hook:
add_action('wp_ajax_la_save_front_editor', array($this, 'save_admin_options'));
The save_admin_options is found L33 and is used to save the plugin’s options:
function save_admin_options(){
if (isset($_REQUEST)) {
update_option( 'la_front_editor', $_REQUEST );
}
die(0);
}
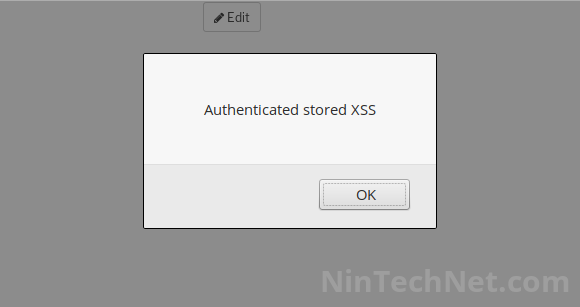
It too lacks a capabilities check and a security nonce. An authenticated user can change the plugin settings. Because the saved data isn’t sanitised, it is also possible to inject JavaScript code into the “btnText” and “disBtntext” variables (text label displayed on the button inside the dashboard Toolbar). The code will be executed when a user is logged in:
Recommendations
We recommend to uninstall this plugin as there isn’t any security patch available. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The vulnerability was reported to the author on September 24, 2020 and the issue was escalated to the WordPress Plugin Team on October 22, 2020. The plugin was removed from the repo on the same day.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
