The WordPress Login or Logout Menu Item plugin, which has 10,000+ active installations, was prone to an unauthenticated options change vulnerability in version 1.1.1 and below.
Reference
CVE-2019-15820
Unauthenticated options change
Login or Logout Menu Item adds a dynamic login/logout menu item to the WordPress front-end. In the “main.php” script, the plugin registers the lolmi_save_settings function via the admin_init hook:
function lolmi_save_settings() {
if(isset($_POST['lolmi_settings_submit'])) {
$login_page_url = (isset($_POST['lolmi_login_page_url']) && !empty($_POST['lolmi_login_page_url'])) ? $_POST['lolmi_login_page_url'] : wp_login_url();
$login_redirect_url = (isset($_POST['lolmi_login_redirect_url']) && !empty($_POST['lolmi_login_redirect_url'])) ? $_POST['lolmi_login_redirect_url'] : home_url();
$logout_redirect_url = (isset($_POST['lolmi_logout_redirect_url']) && !empty($_POST['lolmi_logout_redirect_url'])) ? $_POST['lolmi_logout_redirect_url'] : home_url();
update_option('lolmi_login_page_url', esc_url_raw($login_page_url));
update_option('lolmi_login_redirect_url', esc_url_raw($login_redirect_url));
update_option('lolmi_logout_redirect_url', esc_url_raw($logout_redirect_url));
wp_redirect($_SERVER['REQUEST_URI']."&lolmisaved=true");
die();
}
}
add_action('admin_init', 'lolmi_save_settings');
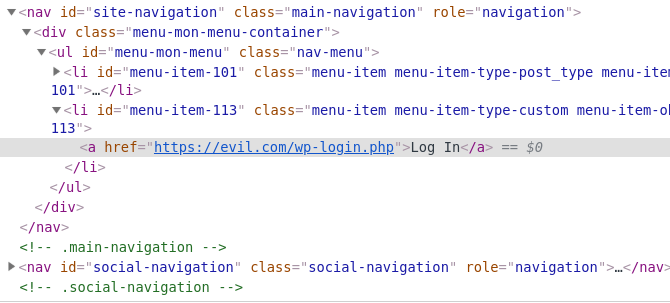
This function, which is used to modify the login URL, lacks capability check and a security nonce and thus is accessible to anyone. An unauthenticated user could change the link to the login URL and redirect users to a malicious website in order to steal their credentials:
Timeline
The vulnerability was discovered and reported to the wordpress.org team on August 04, 2019.
Recommendations
Update as soon as possible if you have version 1.1.1 or below installed.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this type of vulnerability.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
