The WordPress Fruitful theme, which has 9,000+ active installations, was prone to an authenticated stored XSS vulnerability in version 3.8.1 and below.
Authenticated Stored XSS
In the “inc/func/fruitful-function.php” script, the theme registers the fruitful_theme_options_action action via the wp_ajax_* AJAX hook:
add_action('wp_ajax_fruitful_theme_options_action', 'fruitful_data_save');
function fruitful_data_save() {
global $fruitful_theme_options;
$data = $_POST[$fruitful_theme_options->args['opt_name']];
foreach ( $fruitful_theme_options->sections as $section => $data_f ) {
foreach ( $data_f['fields'] as $field ) {
$id = (isset($field['id' ])) ? $field['id'] : '';
$type = (isset($field['type'])) ? $field['type'] : '';
if ($type == 'checkbox') {
if (!isset($data[$id])) {$data[$id] = 'off'; }
}
if ($type == 'textarea') {
if (isset($data[$id])) {$data[$id] = stripslashes($data[$id]);}
}
if (!empty ($field['fields'])) {
foreach ($field['fields'] as $sub_field) {
$id = (isset($sub_field['id' ])) ? $sub_field['id'] : '';
$type = (isset($sub_field['type'])) ? $sub_field['type'] : '';
if ($type == 'checkbox') {
if (!isset($data[$id])) {$data[$id] = 'off'; }
}
if ($type == 'textarea') {
if (isset($data[$id])) {$data[$id] = stripslashes($data[$id]);}
}
}
}
}
}
if (!isset($data['reset'])) {$data['reset'] = 'reset';}
if(!empty($data)) {
if(update_option('fruitful_theme_options', $data)) {
die('1');
} else {
die('0');
}
} else {
die('1');
}
}
The function doesn’t check user capabilities and lacks a security nonce and thus is accessible to any logged-in user. Because some fields like fruitful_theme_options[custom_css] are not sanitized, an attacker can inject JavaScript code into every page and post of the blog:
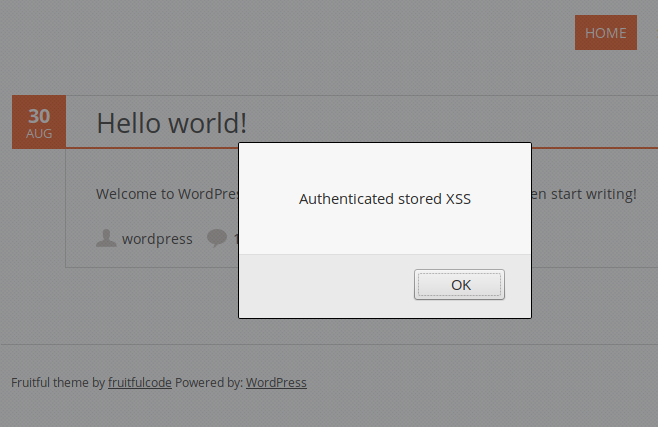
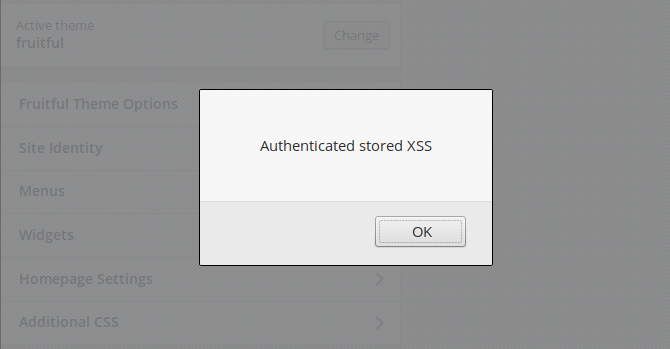
The stored XSS can also be used to target administrators when they edit the theme in the back-end section of WordPress:
Additional Issues
Three other AJAX actions that should be accessible to the administrator only are accessible to any authenticated users:
fruitful_reset_btn: this action will delete the theme options.fruitful_add_new_slide_action: this action only adds one or more input fields while editing the theme. No damage can be done to the website though.run_import_dummy_data: this action will throw a fatal error because it attempts to call another function that does not exist.
Recommendations
Update as soon as possible if you have version 3.8.1 or below installed.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The vulnerability was reported to the wordpress.org team on March 04, 2020 and a new version 3.8.2 was released on March 08, 2020.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
