This is a very interesting spear phishing attack case that we had to deal with this week. Spear phishing are attempts directed at a specific individual, which makes them particularly efficient at harvesting their victim’s credentials (login, password, credit card number etc).
But that one was even more credible: it was made possible due to a vulnerability in the security plugin installed to protect the WordPress blog of the victim.
HTML Injection
The attack targeted a customer running a politically oriented blog and who already faced a couple of attacks in the past. That person was using a premium security plugin only available from Envato’s CodeCanyon website: Swift Security Hide WordPress, Firewall, Code Scanner (v1.4.2.6).
One of its features is to send e-mail alerts when a hacking attempt is blocked, as well as when a WordPress user logs in to the admin dashboard.
A couple of days ago, our customer received such alert:
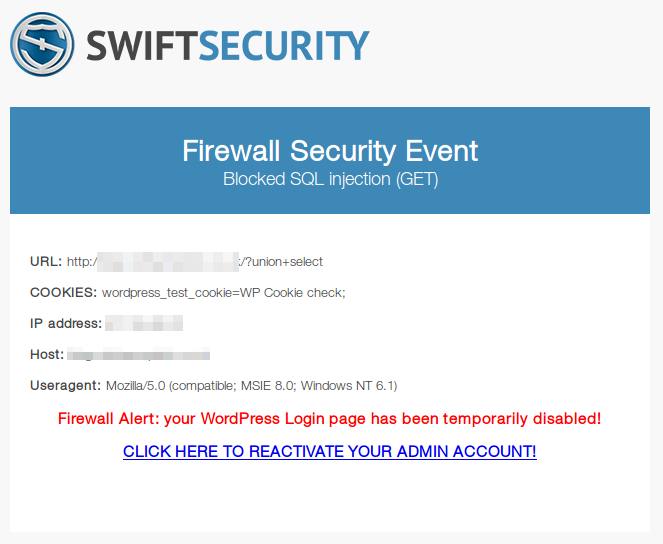
It shows a blocked SQLi attempt (/?union+select), some variables (cookies, attacker IP, host, user-agent), as well as a big and scary warning:
Firewall Alert: your WordPress Login page has been temporarily disabled! CLICK HERE TO REACTIVATE YOUR ADMIN ACCOUNT!
Our customer made sure that the e-mail was truly originating from his blog and plugin (and indeed, it was) before clicking on the link. He was then redirected to the WordPress admin dashboard login page asking for his username and password. Fortunately, he noticed that the login form was not hosted on his own domain but a .co sub-domain instead. Thinking his blog was compromised, he contacted us to sort out the problem.
The first thing we did was to have a look at the HTML e-mail source:
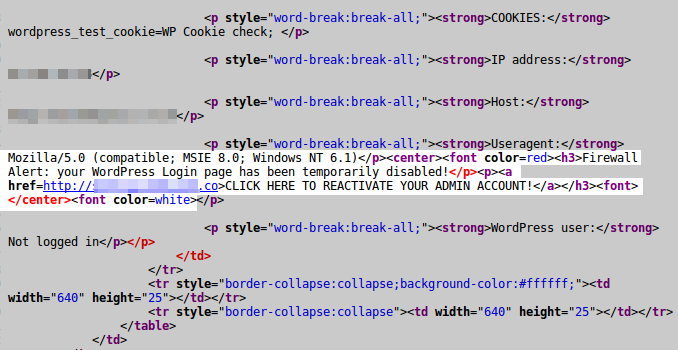
The attacker was able to append HTML code to the User-Agent header. We can even see that he added a <font color=white> tag in order to hide the text from all subsequent paragraphs. A quick look at the HTTP server log shows the full request:
37.44.xxx.xx - - [01/Oct/2015:01:48:03 +0200] "GET /?union+select HTTP/1.1" 403 722 "-" "Mozilla/5.0 (compatible; MSIE 8.0; Windows NT 6.1)</p><center><font color=red><h3>Firewall Alert: your WordPress Login page has been temporarily disabled!</p><p><a href=http://[obscured-URL]>CLICK HERE TO REACTIVATE YOUR ADMIN ACCOUNT!</a></h3><font></center><font color=white>"
The bogus SQLi attempt triggered the firewall which returned a 403 Forbidden HTTP error and sent the e-mail alert including the User-Agent and the HTML code.
This is a very simple but terribly efficient attack, specially when it is sent from your own blog, by your favourite – and trusted – security plugin.
From there, it was obvious that the Swift Security plugin had some serious security issues. We found the following code in SwiftSecurity/classes/SecurityLogObject.class.php:
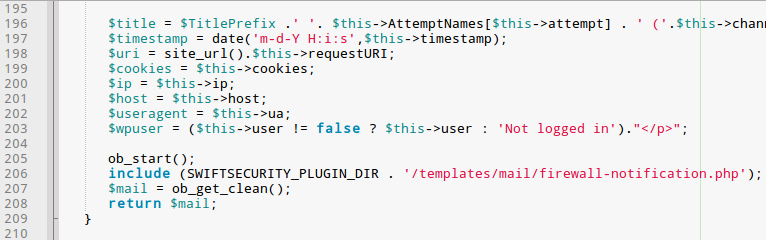
It assigns the user input to variables and then loads
the SwiftSecurity/templates/mail/firewall-notification.php HTML e-mail template:
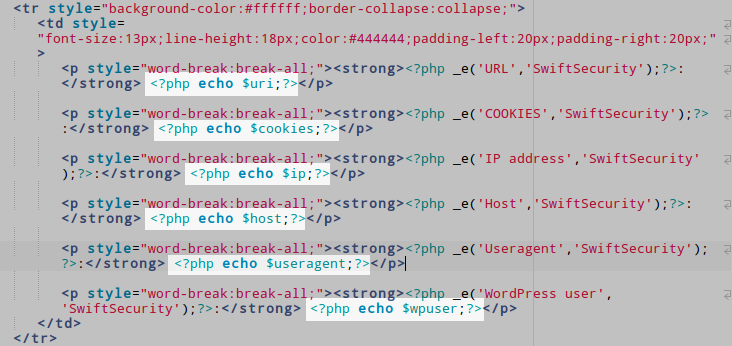
Not all user input are sanitized before being echoed. Vulnerable variables are $useragent and $cookies. Depending on the HTTP server configuration, $host could also be exploited.
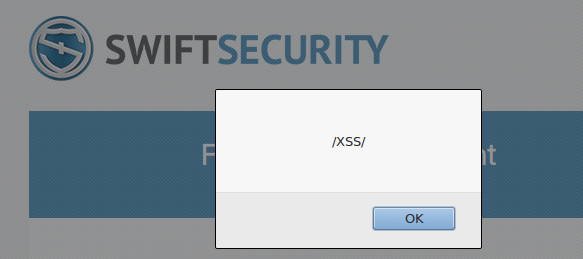
Persistent XSS
In addition to HTML Injection, the plugin is also vulnerable to persistent XSS (Cross-Site Scripting). For instance, an attacker could inject the following JavaScript code: Mozilla/5.0 (compatible)<script>alert(/XSS/);</script>
We informed Envato about that serious vulnerability and it was silently patched by the author in version 1.4.2.7 released on October 07/2015. The changelog does not even make any mention of the security fix, but only “Minor bugfixes”:
07 Oct 2015 - 1.4.2.7 [FIX] Minor bugfixes
