The WordPress TI WooCommerce Wishlist plugin (70,000+ installations) fixed a critical zero-day vulnerability affecting version 1.21.11 and below that could allow an attacker to take over the blog and its database.
This vulnerability is currently being exploited, make sure to update immediately the plugin and to follow the recommendations below.
Authenticated Options Change
On October 13th, two users of our NinjaFirewall plugin contacted us about suspicious activities on their WooCommerce installation that were blocked by the WAF. After reviewing the backtrace created by the firewall, we quickly noticed that there was a critical vulnerability in the TI WooCommerce Wishlist plugin that hackers were attempting to exploit.
The plugin has an import function in the “ti-woocommerce-wishlist/includes/export.class.php” script, loaded with the WordPress admin_action_ hook, that lacks a capability check and security nonce, allowing an authenticated user to modify the content of the WordPress options table in the database. Hackers use it to enable registration by setting the users_can_register option and then create an admin account by changing the default_role option to administrator. It is also possible to redirect all traffic to an external malicious website by changing the siteurl option among other issues. Multiple options can be changed at once.
Despite the fact that, by default, WooCommerce blocks non-admin users from entering the WordPress admin dashboard, hackers bypass the restriction by adding the ?wc-ajax=1 query (which is used to define the DOING_AJAX constant) to the URI:
46.39.91.92 - - [13/Oct/2020:18:48:21 +0200] "POST /wp-admin/?wc-ajax=1 HTTP/1.1"
Because WooCommerce allows customer registration, any logged-in customer can exploit this vulnerability.
Another function in the same script, used to export the configuration, also lacks a capability check and a security nonce.
Recommendations
Update immediately if you are using version 1.21.11 or below. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
If you have been hacked, delete the hacker’s account and double-check the two user registration options from the “WordPress > General Settings” page (as well as the email address located right above them):
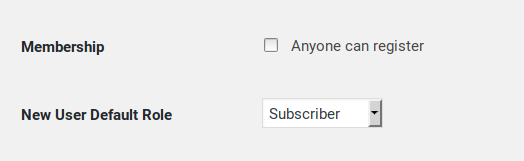
Make sure to search for hidden admin accounts too.
Change all your passwords (WordPress and the database) and scan your site for suspicious files.
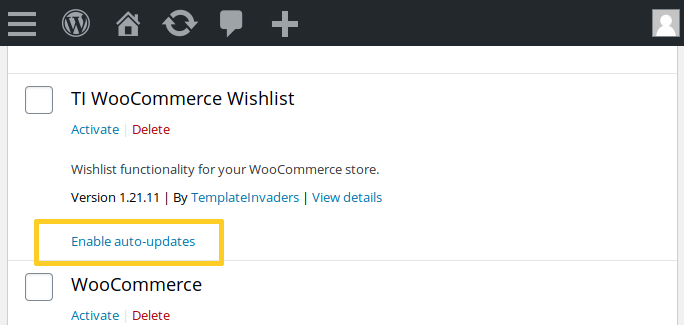
Since v5.5, WordPress has automatic updates for plugins and, unless you log in to your admin dashboard several times a day, I highly recommend to enable that new feature so that if there were a security update available in a plugin, it would be quickly and automatically applied:
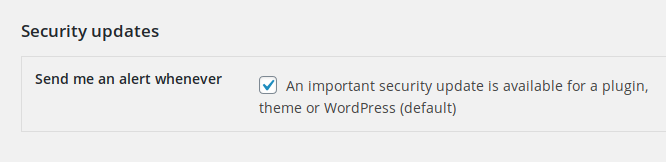
Lastly, if you’re using our NinjaFirewall plugin, you have an option in the “Event Notifications” page to receive a notification when a security update is available. It is enabled by default:
Timeline
The vulnerability was reported to the authors on October 13th, 2020 and a new version 1.21.12 was released on October 16th.
Thanks to Arsyad and Andreas who provided us with NinjaFirewall’s log and backtrace, which helped us to quickly locate and report the vulnerability to the authors.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
