The WordPress Pirate Forms plugin, which has 200,000+ active installations, was prone to an HTML injection vulnerability affecting all email messages sent from its contact form.
A few years ago, we revealed details of an ongoing spear phishing attack that was made possible because of a vulnerability in a security plugin that was installed to protect the WordPress blog of the victim. Pirate Forms v2.5.1 and below was affected by the same type of vulnerability.
Unauthenticated HTML injection
The vulnerable code is located in the ‘public/class-pirateforms-public.php’ script. Lines 592 to 600, if the pirateformsopt_store_ip option is enabled, the plugin retrieves the IP from REMOTE_ADDR and validates it with the PHP filter_var() function, but if there’s an HTTP_X_FORWARDED_FOR variable defined, it will override the IP with that unsafe one, without any validation:
$contact_ip = null;
if ( isset( $pirate_forms_options['pirateformsopt_store_ip'] ) && 'yes' === $pirate_forms_options['pirateformsopt_store_ip'] ) {
$contact_ip = filter_var( $_SERVER['REMOTE_ADDR'], FILTER_VALIDATE_IP );
/* for the case of a Web server behind a reverse proxy */
if ( array_key_exists( 'HTTP_X_FORWARDED_FOR', $_SERVER ) ) {
$contact_ip_tmp = explode( ',', $_SERVER['HTTP_X_FORWARDED_FOR'] );
if ( ! empty( $contact_ip_tmp ) ) {
$contact_ip = array_pop( $contact_ip_tmp );
}
}
// If valid and present, create a link to an IP search
$body['body'][ __( 'IP address', 'pirate-forms' ) ] = $contact_ip;
$body['body'][ __( 'IP search', 'pirate-forms' ) ] = "http://whatismyipaddress.com/ip/$contact_ip";
$body['magic_tags'] += array( 'ip' => $contact_ip );
Because Pirate Forms forwards all email messages sent from the contact form to the admin mailbox using HTML format by default, any HTML code can be inserted into the template. For instance, an unauthenticated attacker can inject into the email body a link pointing to a malicious login page URL in an attempt to steal the administrator credentials:
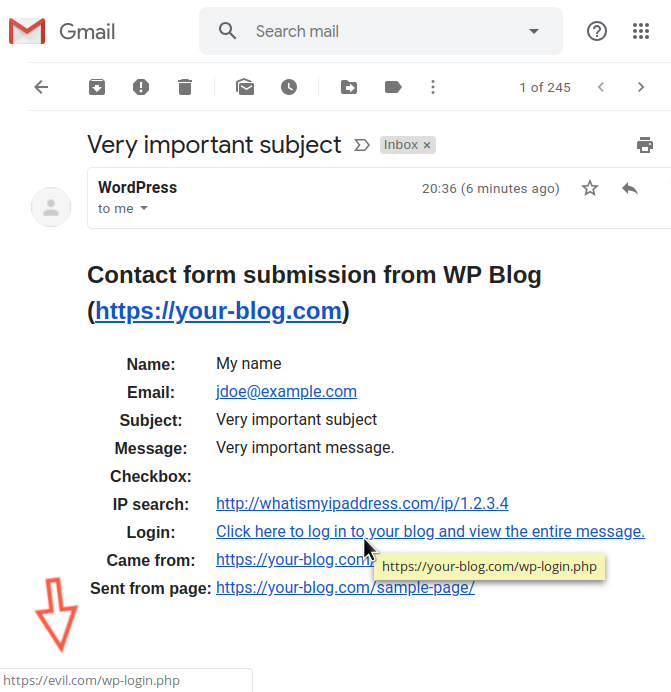
A CSRF attack could also be used against an authenticated administrator in order to trick the victim into performing an undesired action on their own website (that’s why, if you’re a WordPress plugin or theme developer, you should use security nonces to block this type of attack).
Timeline
The vulnerability was discovered and reported to the wordpress.org team on July 26, 2019.
Recommendations
Update as soon as possible if you have version 2.5.1 or below installed.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected.
NinjaFirewall protects proactively against this type of vulnerability.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
