The WordPress Newsletter Manager plugin (5,000+ active installations) is prone to an insecure deserialization vulnerability affecting version 1.5.1 and below that could lead to unauthenticated PHP object injection.
This plugin is not maintained anymore and the vulnerability has never been fixed. Make sure to follow the recommendations below.
Insecure Deserialization
In the “subscription.php” script line 31, the customFieldsDetails input is passed to the unserialize function:
if(isset($_REQUEST['postFrom']) && $_REQUEST['postFrom'] == 'cfm'){
$xyz_em_email = rawurldecode(sanitize_email(stripslashes(trim($_REQUEST['xyz_em_email']))));
$customFieldsDetails = unserialize(rawurldecode(stripslashes_deep(xyz_trim_deep($_REQUEST['customFieldsDetails']))));
$xyz_em_name = $customFieldsDetails[0];
An unauthenticated user could inject a serialized PHP object when submitting the subscription form, which could potentially lead to a PHP object injection vulnerability.
Timeline
The vulnerability was reported to the WordPress Plugin Team on October 28, 2020, and the plugin was removed from the repo on the same day.
Recommendations
We recommend to uninstall this plugin as there isn’t any security patch available. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability. Additionally, NinjaFirewall has an option to block serialized PHP objects, which I recommend to enable:
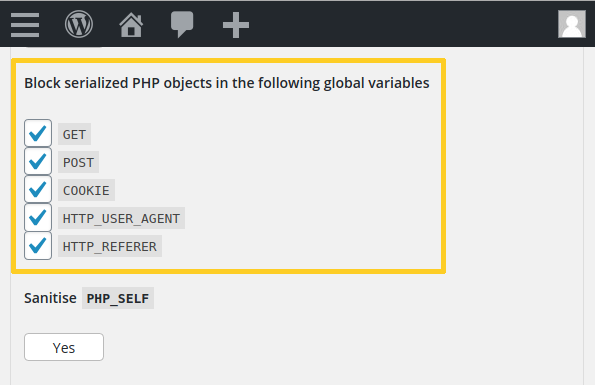
It can be found in the “Firewall Policies > Advanced Policies” section.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
