Multiple plugins offering to convert WordPress’ default plain text emails to HTML format were found to be vulnerable to HTML injection, which could lead to phishing or CSRF attacks targeting the administrator.
Reference
A CVE ID has been requested and we’ll update this post when it is assigned.
Vulnerable plugins
- Email Templates <=1.3 (20,000+ active installations)
- WP HTML Mail – Email Designer <=2.9.0.3 (10,000+ active installations)
- WP Email Template <=2.2.10 (5,000+ active installations)
HTML Injection
Those plugins convert the default plain text emails sent by WordPress to HTML format. However, they take the content of the “text/plain” part and turn it into a new “text/html” part without sanitising it. That can lead to HTML injection and can be used for phishing and CSRF attacks targeting the administrators because it affects all messages sent by the blog, its plugins and themes (e.g., contact form, comment, notification etc).
Here’s an example of a malicious message posted using the WordPress default comment form:
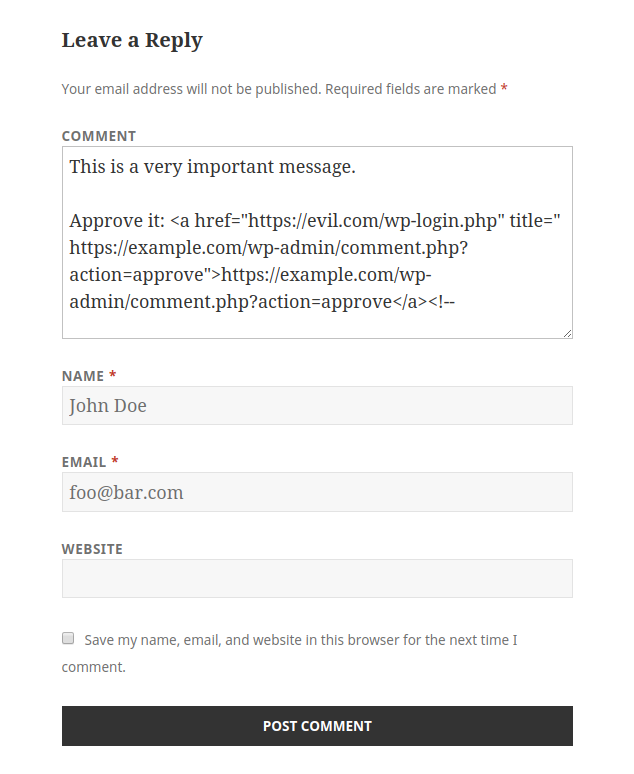
Because WordPress sends plain text emails, it doesn’t need to sanitise the body, and thus the administrator will receive the following message:
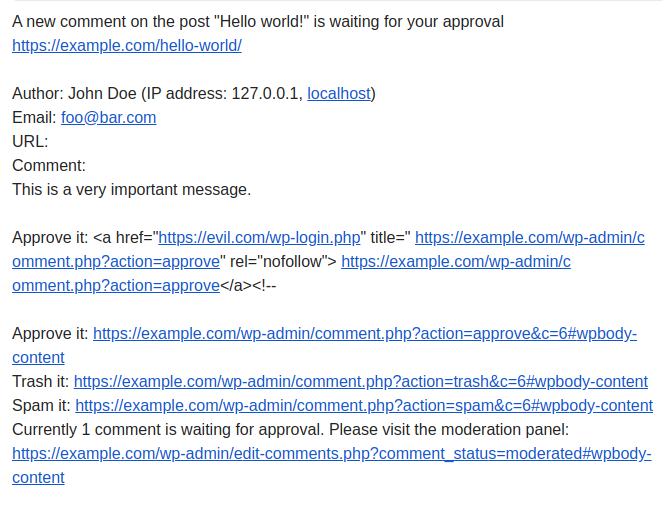
Obviously, the attempt to trick the admin into clicking on the malicious link is so plain to see that the attacker doesn’t stand a chance.
But it’s a whole different story when the same message is sent, unsanitised, using one of the above plugins:
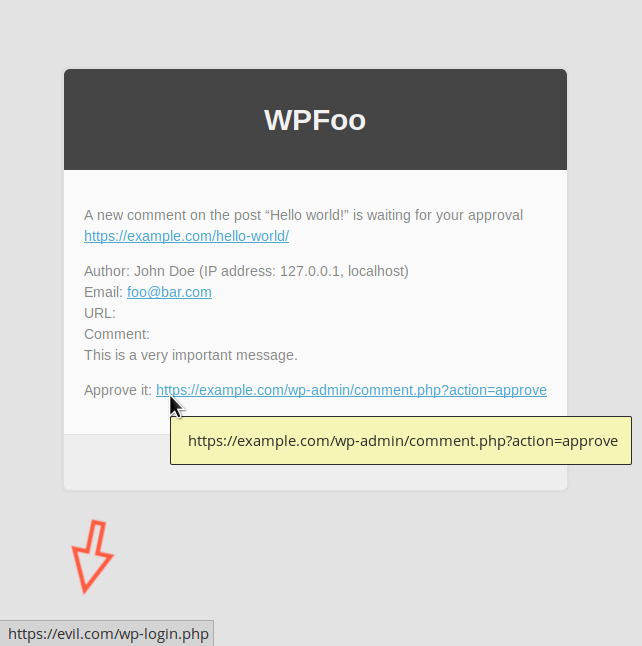
Timeline
The vulnerabilities were discovered and reported to the wordpress.org team on October 16, 2019.
Recommendations
Update any of the above plugins to the latest available version.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
