The WordPress B2BKing plugin (14,000+ installs) was proned to several broken access control vulnerabilities in version 4.6.00 and below that could allow customers to change the price of all products among other issues.
Authenticated Product Price Change
CVSS v3.1: 6.5 (Medium)
In the “b2bking/includes/class-b2bking.php” script, the “b2bkingdownloadpricelist” function is accessible via the WordPress AJAX API:
add_action( 'wp_ajax_nopriv_b2bkingdownloadpricelist', array($this, 'b2bkingdownloadpricelist') ); add_action( 'wp_ajax_b2bkingdownloadpricelist', array($this, 'b2bkingdownloadpricelist') );
It is used to download a CSV file of all WooCommerce products and their corresponding price:
function b2bkingdownloadpricelist(){
// Check security nonce.
if ( ! check_ajax_referer( 'b2bking_security_nonce', 'security' ) ) {
wp_send_json_error( 'Invalid security token sent.' );
wp_die();
}
...
The function only verifies the b2bking_security_nonce nonce but has no capability check to restrict access to it. Although the nonce shouldn’t be required (a CSRF attack on the CSV file download action wouldn’t really make sense) it is the only safeguard. However, it leaks in the page source of the WordPress dashboard because it is loaded via the admin_enqueue_scripts hook, allowing a customer to download the CSV file:
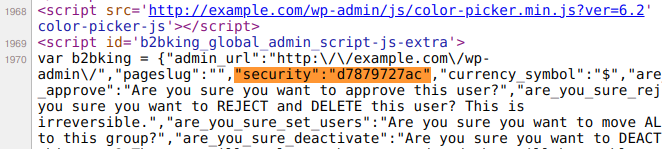
Then, the customer can tamper with that file and reupload it because the “b2bking_save_price_import” function, which is loaded via the admin_post_ hook and thus accessible to all logged-in users, doesn’t have a capability check and a security nonce to restrict the access to high privileged users only:
// Price Importer Processing add_action( 'admin_post_b2bking_price_import', array($this, 'b2bking_save_price_import') );
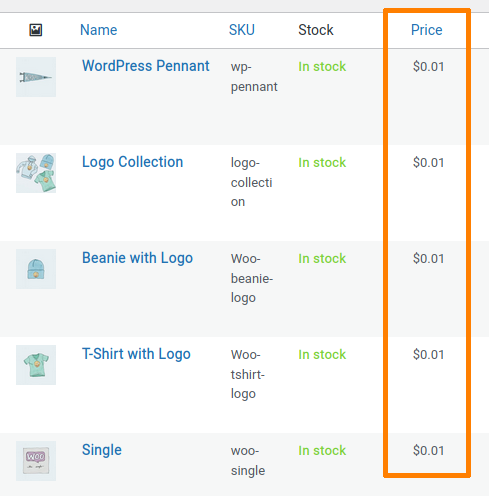
A customer, or any logged-in user, can modify all WooCommerce products price before placing an order:
Additional Issues
Many AJAX actions in the “b2bking/includes/class-b2bking.php” script rely on the leaked b2bking_security_nonce nonce only and lack a capability check although they should be accessible to the shop manager only.
Recommendations
Update immediately if you have version 4.6.00 or below installed. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The vulnerabilities were reported to the developers on May 11, 2023, and a new version 4.6.20 was released on May 27, 2023.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
