The WordPress FlyingPress plugin fixed an authenticated broken access control vulnerability affecting version 3.9.6 and below.
Broken Access Control
CVSS v3.1: 7.6 (High)
The plugin registers nine different AJAX actions in the FlyingPress\Ajax::init method. They all lack a capability check and a security nonce, allowing an authenticated user to interact with the plugin.
Among those actions, save_config is used to save the plugin configuration, which includes an option to use an external CDN. When enabled, the plugin rewrites static files URL (e.g., JavaScript, CSS) to deliver them from the CDN instead of the current domain.
An authenticated user such as a subscriber or a WooCommerce customer could use that AJAX action to enable the CDN feature and replace the source of static elements by injecting a rogue domain, which could be used to redirect all traffic to an external malicious site for instance:
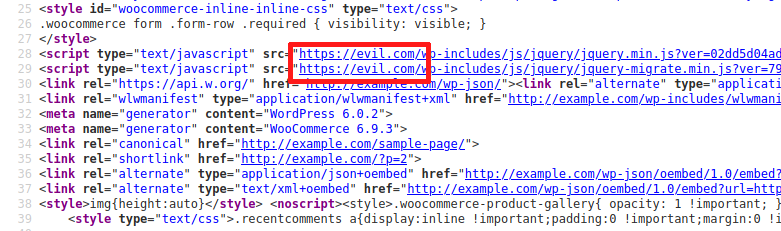
The domain will be injected into all pages and posts in the front-end.
Recommendations
Update immediately if you have version 3.9.6 or below installed. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The issue was reported to the developers on October 05, 2022 and a new version 3.9.7 was released on November 14, 2022.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
