The WordPress Ultimate Addons for Gutenberg plugin (200,000+ active installations) fixed an authenticated settings change vulnerability affecting version 1.14.7 and below.
The plugin registers six AJAX actions in the “ultimate-addons-for-gutenberg/classes/class-uagb-admin.php” script: uagb_activate_widget, uagb_deactivate_widget, uagb_bulk_activate_widgets, uagb_bulk_deactivate_widgets, uagb_allow_beta_updates and uagb_file_generation.
All of them have a very similar structure: they lack capability checks and rely only on the same uagb-block-nonce nonce. For instance, the activate_widget function:
public static function activate_widget() {
check_ajax_referer( 'uagb-block-nonce', 'nonce' );
$block_id = sanitize_text_field( $_POST['block_id'] );
$blocks = UAGB_Helper::get_admin_settings_option( '_uagb_blocks', array() );
$blocks[ $block_id ] = $block_id;
$blocks = array_map( 'esc_attr', $blocks );
// Update blocks.
UAGB_Helper::update_admin_settings_option( '_uagb_blocks', $blocks );
UAGB_Helper::create_specific_stylesheet();
echo $block_id;
die();
}
The nonce is populated in the styles_scripts function and needs to be echoed when a logged-in administrator visits the plugin’s settings page (wp-admin/options-general.php?page=uag):
// Enqueue admin scripts.
if ( isset( $_REQUEST['page'] ) && UAGB_SLUG === $_REQUEST['page'] ) {
add_action( 'admin_enqueue_scripts', __CLASS__ . '::styles_scripts' );
self::save_settings();
}
However, because the plugin relies on $_REQUEST['page'] while WordPress relies on $_GET['page'], any authenticated user could send a $_POST['page'] = 'uag' to the current page, WordPress would ignore it but Ultimate Addons for Gutenberg would catch it and leak the security nonce in the source of the page, allowing the user to interact with all six AJAX actions:
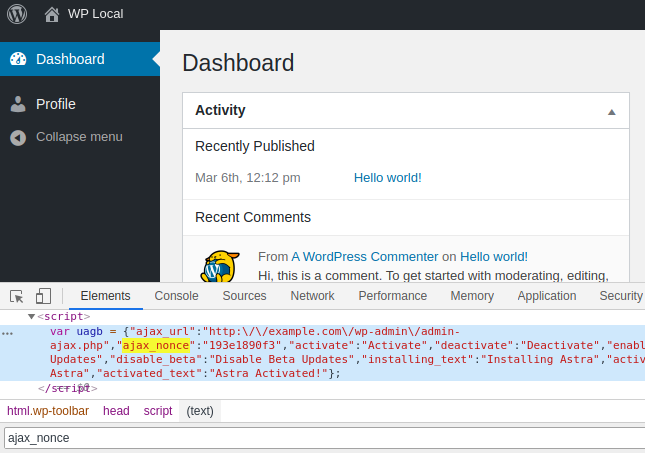
Recommendations
Update the plugin if you have version 1.14.7 or below installed.
Timeline
The vulnerability was reported on March 26, 2020 and a new version 1.14.8 was released on March 30, 2020.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
