The WordPress Lara Google Analytics plugin, which has 20,000+ active installations, was prone to an authenticated stored XSS vulnerability in version 2.0.4 and below.
This vulnerability is currently being exploited, make sure to follow the recommendations below.
Reference
A CVE ID has been requested and we’ll update this post when it is assigned.
Authenticated Stored XSS
In the main “lara-google-analytics.php” script, the lrgawidget_setProfileID action is used to call the lrgawidget_callback function via the WordPress AJAX API.
add_action( 'wp_ajax_lrgawidget_setProfileID', 'lrgawidget_callback' );
...
...
function lrgawidget_callback() {
global $wpdb;
$user_id = get_current_user_id();
$lrperm = lrgawidget_internal_permissions();
$lrdata = $_POST;
$modifiedAction = explode("_", $lrdata['action']);
$lrdata['action'] = $modifiedAction[1];
if ($lrdata['action'] == "setProfileID"){
if ( (isset($lrdata['enable_universal_tracking'])) && !empty($lrdata['property_id'])){
update_option('lrgawidget_property_id', $lrdata['property_id']);
}else{
delete_option('lrgawidget_property_id');
}
}
...
...
Attackers are using it to inject JS code in the property_id field. It is injected into all pages and posts of the CMS:
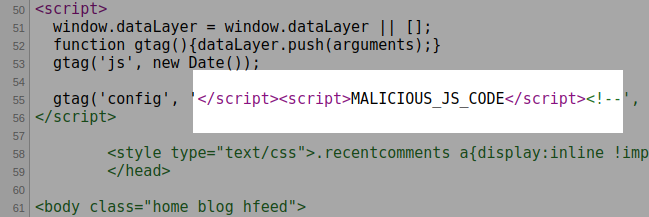
Note that the attack requires a user account on the blog, such as a subscriber.
Timeline
The vulnerability was reported to the wordpress.org team on October 13, 2019, and a new version 2.0.5 was released the same day.
Recommendations
Update as soon as possible if you have version 2.0.4 or below installed.
Note that the new version was released only a few hours after we reported the issue – which is a great thing – and it does block the ongoing attack, however it still lacks capability check and hopefully the author will come up with a better patch in the next few days.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Stay informed about the latest vulnerabilities in WordPress plugins and themes: @nintechnet
