Eight WordPress plugins were prone to an authenticated arbitrary plugin installation vulnerability, among other issues.
Vulnerable Plugins
- Events Shortcodes For The Events Calendar <=1.9.4 (10k+ installations)
- Cryptocurrency Widgets – Price Ticker & Coins List <=2.4 (10k+ installations)
- Cryptocurrency Donation Box – Bitcoin & Crypto Donations <=1.7 (5k+ installations)
- The Events Calendar Widgets For Elementor <=1.4.3 (5k+ installations)
- Event Single Page Templates Addon For The Events Calendar <=1.5 (3k+ installations)
- The Events Calendar Search Addon <=1.1.3 (2k+ installations)
- The Events Calendar Countdown Addon <=1.3.1 (2k+ installations)
- Cryptocurrency Widgets For Elementor <=1.2.1 (1k+ installations)
Additional plugins:
- Cool Timeline <=2.3.3 (+20k installations): although this plugin includes the same vulnerability, it isn’t exploitable because of a coding error in the vulnerable function.
Authenticated arbitrary plugin installation
CVSS v3.1: 8.8 (High)
As all plugins include the same vulnerability (scripts and actions name may differ from one another), I’ll review the “Events Shortcodes For The Events Calendar” plugin in this advisory.
In the admin/events-addon-page/events-addon-page.php script, the plugin loads the cool_plugins_install fuction via an authenticated cool_plugins_install_the-events-calendar AJAX action:
add_action('wp_ajax_cool_plugins_install_'. $this->plugin_tag, array($this, 'cool_plugins_install'));
The function is used to download a remotely hosted plugin, in ZIP archive format, and to extract its content into the WordPress plugins folder:
/**
* handle ajax for installing plugin from the dashboard.
* This function use the core wordpress functionality of installing a plugin through URL
*/
function cool_plugins_install(){
if( isset( $_POST['wp_nonce'] ) && isset( $_POST['nonce_name'] ) && wp_verify_nonce( $_POST['wp_nonce'] , $_POST['nonce_name'] )){
require_once 'includes/cool_plugins_downloader.php';
$downloader = new cool_plugins_downloader();
return $downloader->install( $_REQUEST['url'], 'install' );
}else{
die('wp nonce verification failed!');
}
die();
}
The function lacks a capability check, and the name and value of the security nonce ($_POST['wp_nonce'] and $_POST['nonce_name']) are user input.
An authenticated user can retrieve any nonce in the source of the HTML page, such as the WordPress log out nonce, use it to bypass the check, and download and extract a remote ZIP file on the blog, which can lead to remote code execution:
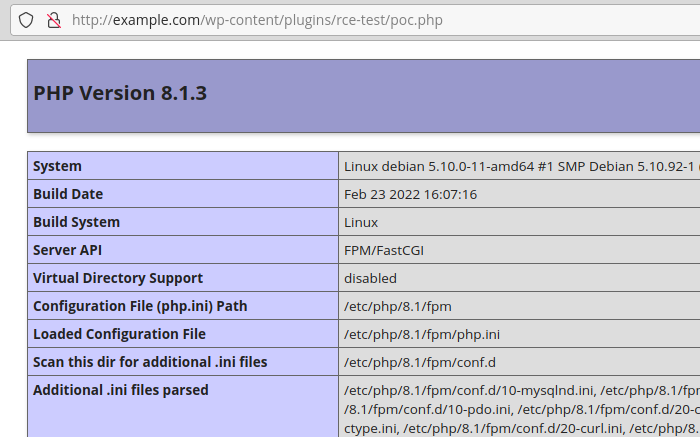
Additional issues
All plugins, including Cool Timeline, were prone to an authenticated plugin activation vulnerability.
Recommendations
Update immediately if you have the vulnerable versions installed on your blog. If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Timeline
The issue was discovered and reported to the WordPress Plugin Team on April 1st, 2022.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
