The WordPress Easy WP SMTP plugin, which has 500,000+ active installations, fixed a zero-day vulnerability affecting version 1.4.2 and below that could allow an unauthenticated user to reset the admin password among other issues.
This vulnerability is currently exploited, make sure to update as soon as possible to the latest version.
The Easy WP SMTP plugin has an optional debug log where it writes all email messages (headers and body) sent by the blog. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/”. The log is a text file with a random name, e.g., 5fcdb91308506_debug_log.txt. The plugin’s folder doesn’t have any index.html file, hence on servers that have directory listing enabled, hackers can find and view the log:
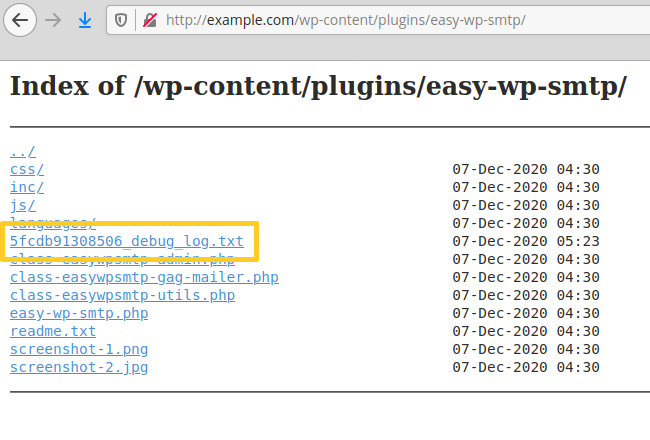
Then, they perform the usual username enumeration scans to find the admin login name, for instance via the REST API:
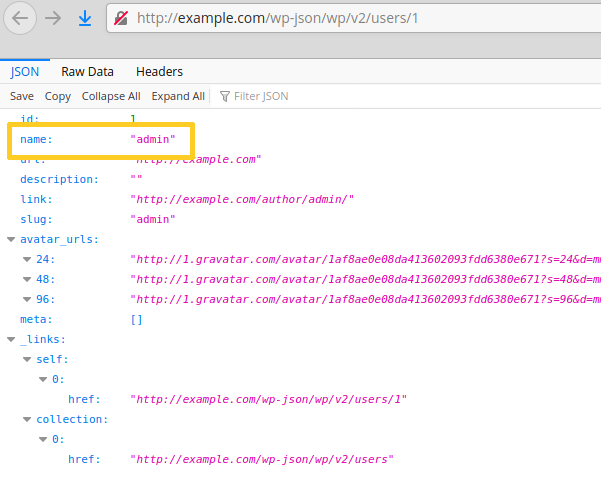
Hackers can also perform the same task using author achive scans (/?author=1).
They access the login page and ask for the reset of the admin password:
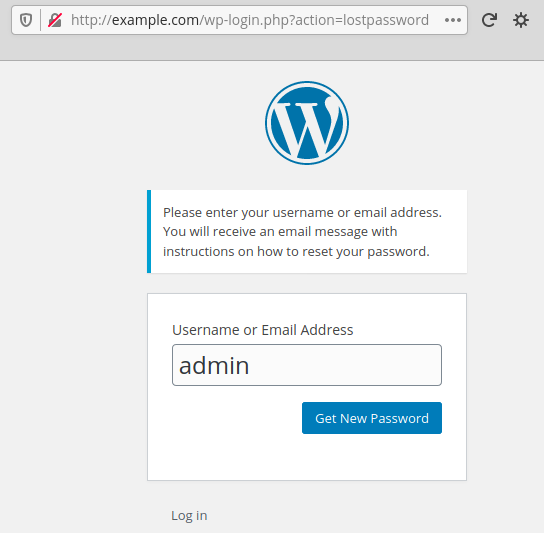
Then, they access the Easy WP SMTP debug log again in order to copy the reset link sent by WordPress:
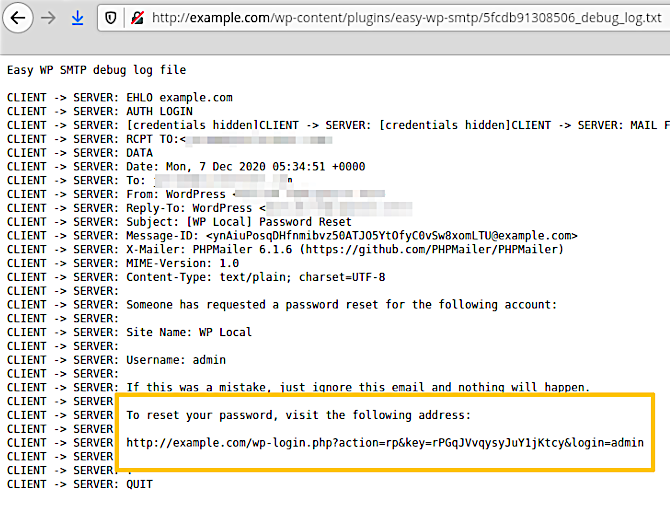
With that link, they reset the admin password:
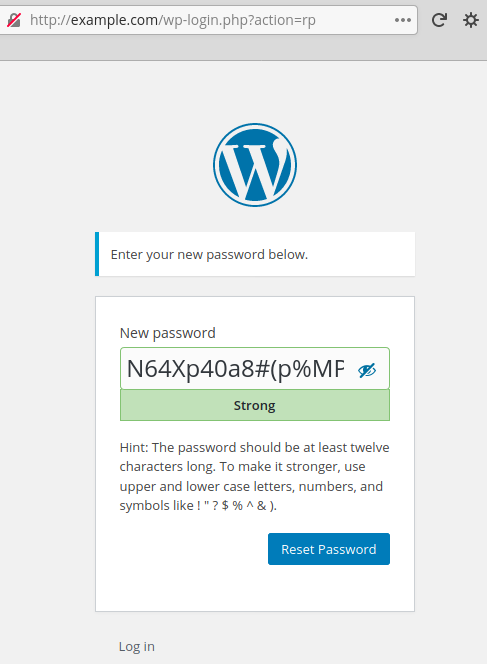
They log in to the admin dashboard and, on all WordPress hacked sites we saw, they immediately install rogue plugins on the blog.
Recommendations
Update immediately if you have version 1.4.2 or below installed.
Consider disabling the debug log, as it could leak sensitive information (messages, passwords etc).
If you are using our web application firewall for WordPress, NinjaFirewall WP Edition (free) and NinjaFirewall WP+ Edition (premium), you are protected against this vulnerability.
Stay informed about the latest vulnerabilities
- Running WordPress? You can get email notifications about vulnerabilities in the plugins or themes installed on your blog.
- On Twitter: @nintechnet
